- https://github.com/OWASP/MSTG-Hacking-Playground/wiki/Android-App#omtg_datast_001_badencryption
- https://github.com/OWASP/MSTG-Hacking-Playground/tree/master/Android/MSTG-Android-Java-App/app
The intent here is to show why is it necessary to use proper Encryption libraries and functions and do not try to create your own encryption algorithms which might be easily reverse engineered.
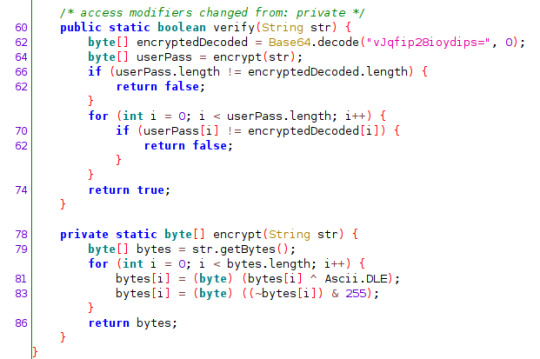
As we can see the verify method compares the two encrypted secret byte by byte and it returns false if there’s a mismatch.
The encrypt() method uses XOR for encryption, here’s a great video on the subject Symmetric Key Cryptography: The XOR Cipher
Run frida-server on the target device and hook onto the encrypt() method with objection and interact with the application
adb shell “su -c /data/local/tmp/frida-server”
objection -g sg.vp.owasp_mobile.omtg_android explore
android hooking watch class_method sg.vp.owasp_mobile.OMTG_Android.OMTG_DATAST_001_BadEncryption.encrypt --dump-args --dump-return
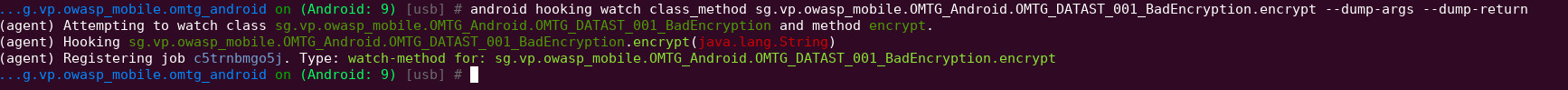
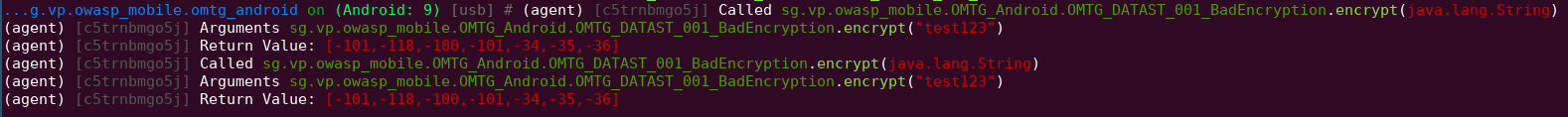
The encrypt method would look like this in python
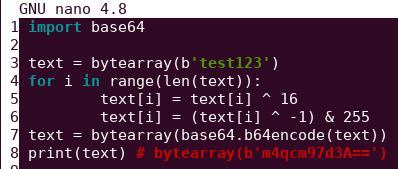
The decrypt method would look like this in python
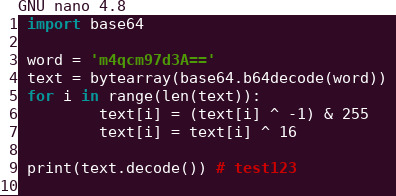
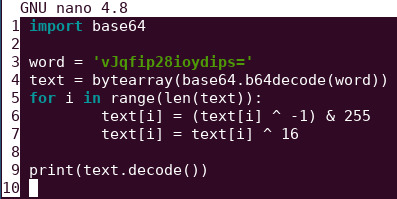
Therefore we just have to supply the hard-coded base64 value to get the secret
Tools used