- https://github.com/OWASP/MSTG-Hacking-Playground/wiki/Android-App#omtg_datast_011_memory
- https://github.com/OWASP/MSTG-Hacking-Playground/tree/master/Android/MSTG-Android-Java-App/app
The intent here is to show that a memory dump can leak sensitive information like decrypted information or keys.
Take a look at the source code
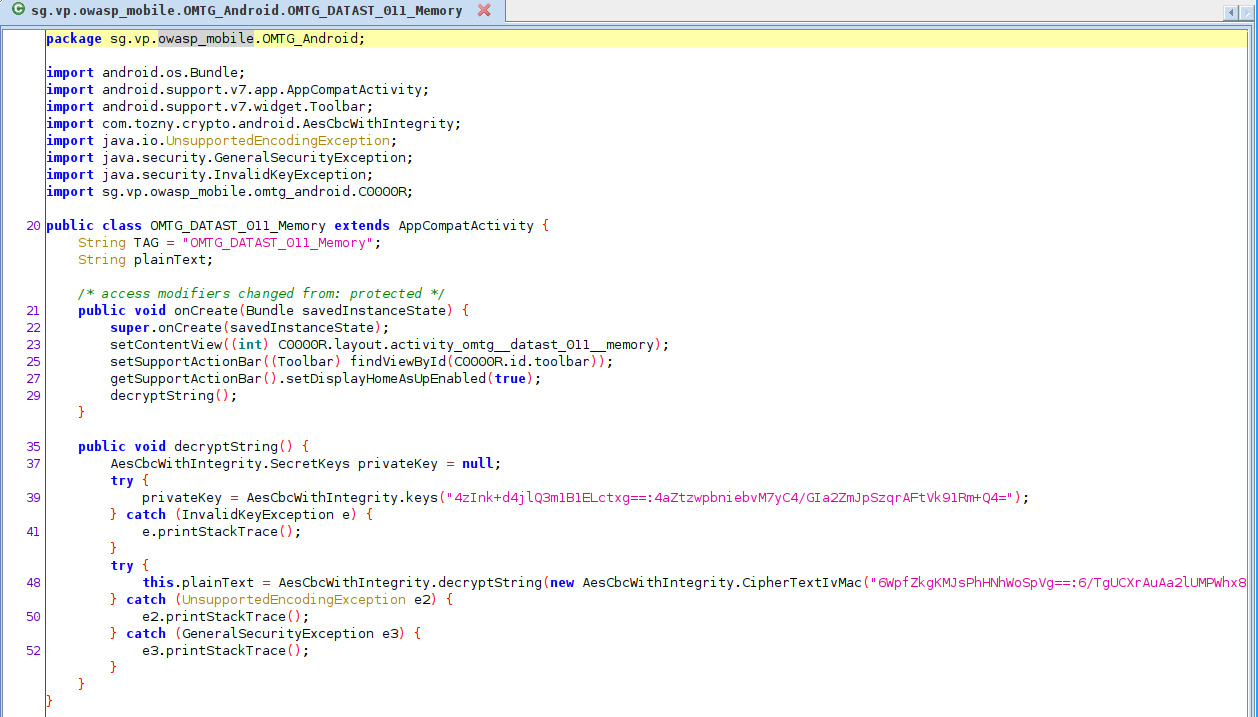
Here we have to dump the memory and identify the function (decryptString()) which was called for this activity and get the decrypted string.
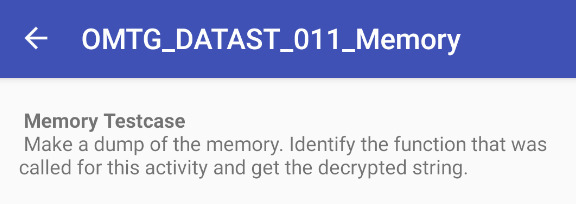
Lets fire up frida and do a memory dump with fridump
adb shell “su -c /data/local/tmp/frida-server”
frida-ps -Ua
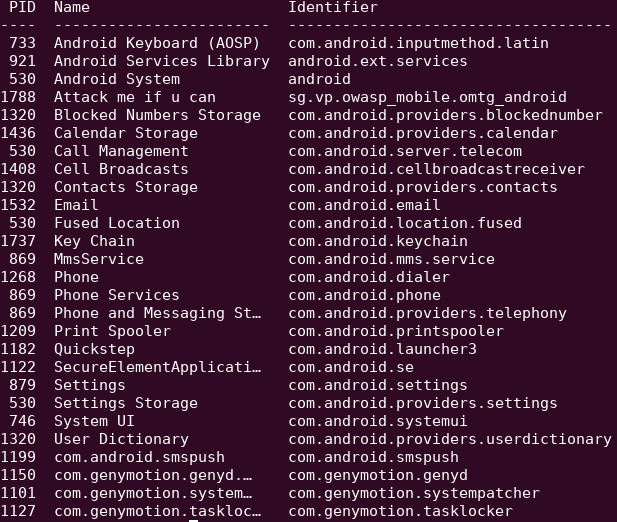
python3 fridump.py -U sg.vp.owasp_mobile.omtg_android -s
cd to fridump/dump
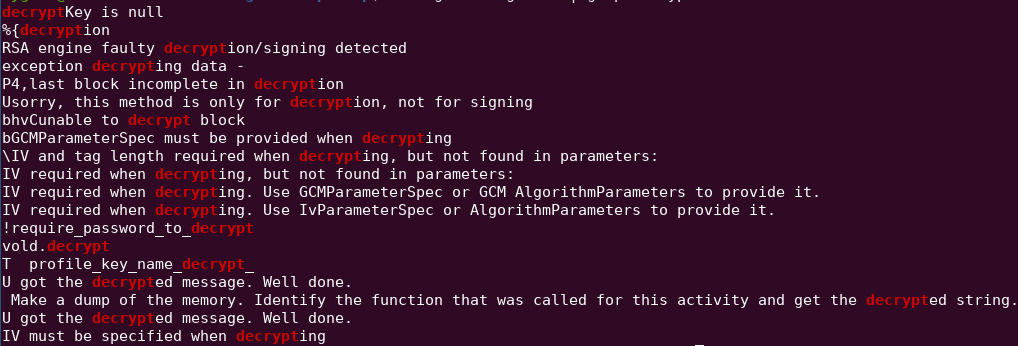
strings strings.txt | grep decrypt
Tools used