- https://github.com/OWASP/MSTG-Hacking-Playground/wiki/Android-App#omtg_datast_001_sqlite_not_encrypted
- https://github.com/OWASP/MSTG-Hacking-Playground/tree/master/Android/MSTG-Android-Java-App/app
The intent here is to show that no sensitive information should be stored in a SQLite database as it is stored by default in clear text.
Take a look at the source code
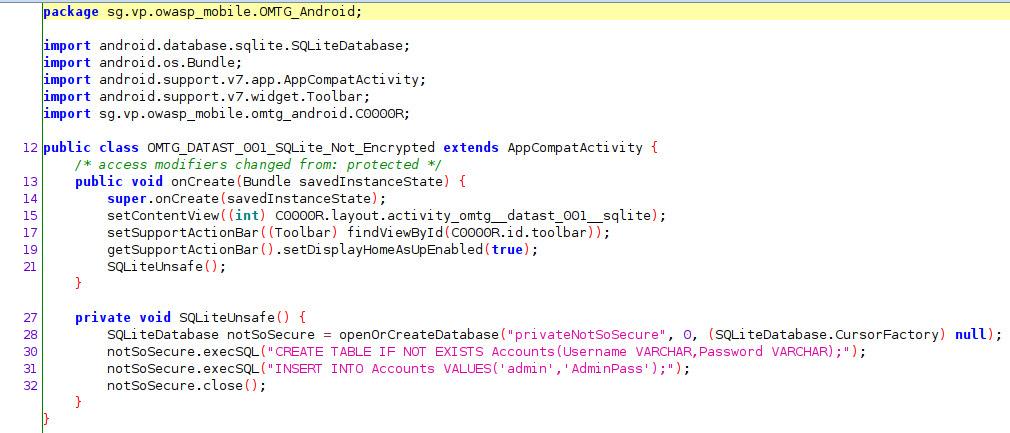
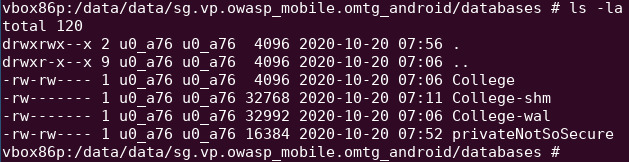
Line 28 indicates that we should look for a database called “privateNotSoSecure” in /data/data/sg.vp.owasp_mobile.omtg_android/databases
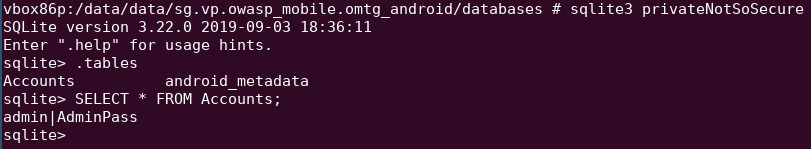
Open the database with sqlite3:
sqlite3 privateNotSoSecure
List tables:
.tables
Dump everything in table “Accounts”:
SELECT * FROM Accounts;
Tools used