- https://github.com/OWASP/MSTG-Hacking-Playground/wiki/Android-App#omtg_datast_001_sqlite_encrypted
- https://github.com/OWASP/MSTG-Hacking-Playground/tree/master/Android/MSTG-Android-Java-App/app
- https://github.com/OWASP/owasp-mstg/blob/master/Document/0x05c-Reverse-Engineering-and-Tampering.md#reviewing-disassembled-native-code
It is a best practice to encrypt the SQLite database, but the problem is where to store the key. This shows that there is no way to hide a key locally against an attacker. If the key is stored locally it can be recovered, even though resilience countermeasures can be in place to slow down the attacker. To mitigate saving the key locally, the following two approaches can be considered:
- ask for a password when the app starts that is used to generate the key (likely to be prone to brute force attacks if the password is weak)
- or store the key on the server, then the app can only be used if the app is online.
So we know that a native library which stores an encryption key is loaded from /lib.
First of all decode the .apk with apktool
apktool d app-arm-debug-Android5.apk
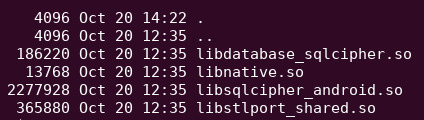
List the contents of /lib
ls -la app-arm-debug-Android5/lib/armeabi/
Take a look at the source code to determine what we should look for in the native libraries
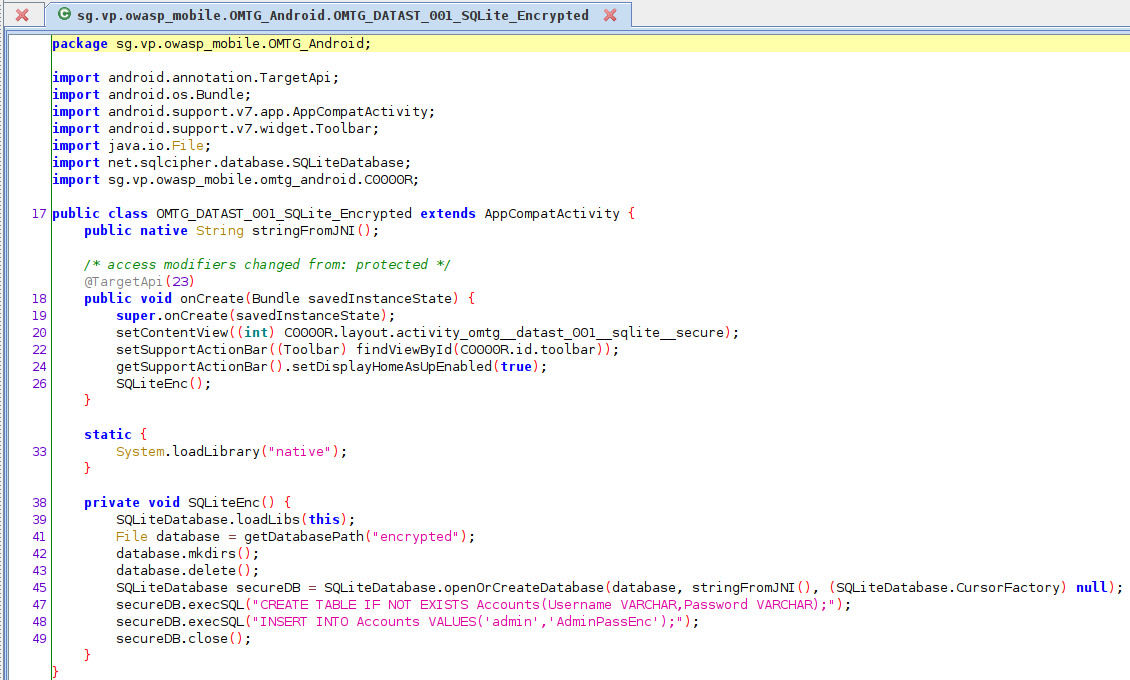
Based on this we should look for JNI related symbols in the native library. Let’s fire up radare2. Open libnative.so in radare2
r2 libnative.so
Grep for any JNI related symbols
is~Java
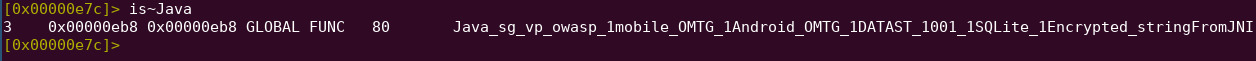
The function we have to disassemble is at address 0x00000eb8
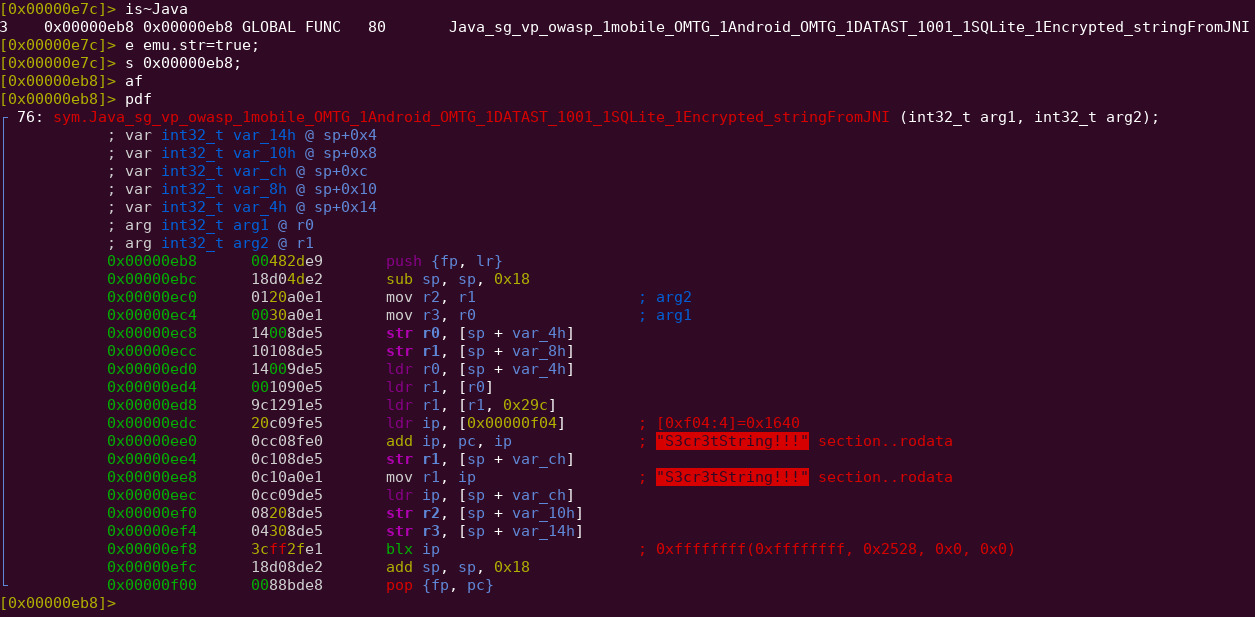
Enable radare2′s string emulation
e emu.str=true;
Seek to address 0x00000eb8
s 0x00000eb8
Analyze and print disassembly of function
af
pdf
Tools used