- https://github.com/OWASP/MSTG-Hacking-Playground/wiki/Android-App#omtg_datast_001_internalstorage
- https://github.com/OWASP/MSTG-Hacking-Playground/tree/master/Android/MSTG-Android-Java-App/app
The intent here is to show that storing data on the device itself can lead to disclosure of data. Usage of internal storage should not be used for sensitive information.
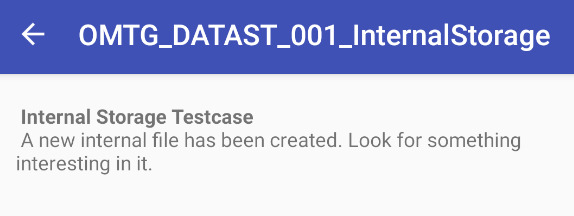
Take a look at the source code
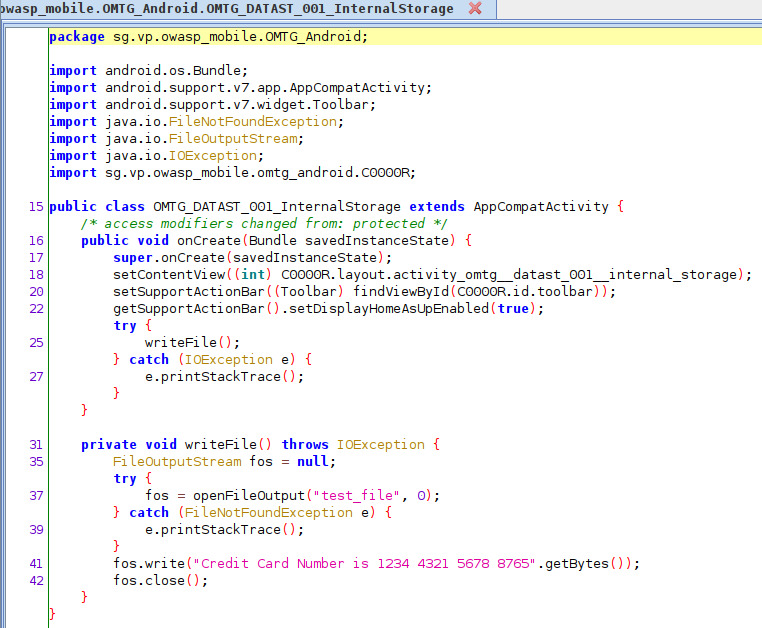
Line 37 indicates that we should look for a file called “test_file” in the internal storage (/data/data/sg.vp.owasp_mobile.omtg_android) of the application.
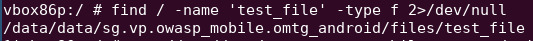
Connect to the target device via adb and use find
adb shell
find / -name ‘test_file’ -type f 2>/dev/null
Tools used