In the realm of penetration testing, Command and Control (C2 or C&C) refers to the infrastructure used by attackers to communicate with compromised systems in a target network during a penetration test or cyberattack.
In this series of articles I'll go through the exercises found in the book Advanced Penetration Testing by Wil Allsopp, other posts can be found at:
APT Insights Part 1: VBA and VBS
APT Insights Part 2: Command and Control
As I progress through the book I'll try to find alternative solutions for the outdated methods/techniques, since the book was published in 2017 not all examples will work out-of-the-box. Despite the year of publication and based on the reviews the book is still a relevant entry-level read for those who want to gain insight into advanced penetration testing and how advanced persistent threats work behind the scenes.
Disclaimer: This content is for educational purposes only. The techniques and tools discussed are intended solely for ethical and legal penetration testing, and security research within the bounds of the law. Unauthorized use of these techniques on systems and networks that you do not own or have explicit permission to test is illegal and unethical. The author and publisher disclaim any responsibility for any misuse or damage resulting from the application of the information provided.
Exercises from the book
- Implement the C2 infrastructure as described in Chapter 1 using C and libssh. Alternatively, use whatever programming language and libraries you are familiar with.
- Implement a C2 dropper in VBS that downloads a custom payload as shellcode rather than as an .exe and injects it directly into memory. Use the API calls from the initial VBA script.
- Assuming your payload had to be deployed as shellcode within a VBA script, how would you obfuscate it, feed it into memory one byte at a time, and execute it? Use VirusTotal and other resources to see how AV engines react to these techniques.
Setting up Visual Studio and vcpkg
- Download Visual Studio Community edition here: https://visualstudio.microsoft.com/vs/
- When configuring the installation make sure
Desktop development with C++is checked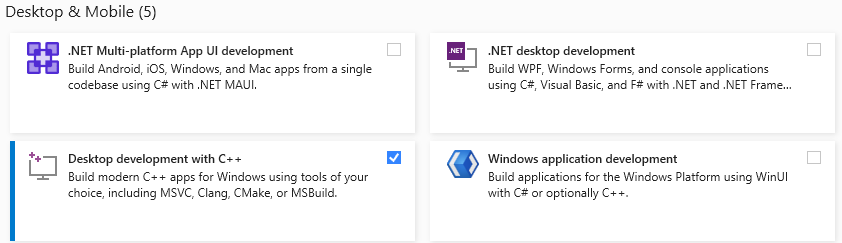
- Get vcpkg and follow the installation guide
- Get
libsshwithvcpkg
PS C:\dev\vcpkg> .\vcpkg.exe search libssh
curl[ssh] SSH support via libssh2
ffmpeg[ssh] SFTP protocol via libssh
libgit2[ssh] SSH support via libssh2
libssh 0.10.5#1 libssh is a multiplatform C library implementing the SSHv2 protocol on cli...
libssh[zlib] libssh with zlib
libssh2 1.11.0#1 libssh2 is a client-side C library implementing the SSH2 protocol.
libssh2[openssl] Use the openssl crypto backend
libssh2[zlib] Use compression via zlib
PS C:\dev\vcpkg> .\vcpkg.exe install libssh
Computing installation plan...
A suitable version of cmake was not found (required v3.29.2) Downloading portable cmake 3.29.2...
Downloading cmake...
[...SNIP...]
- In order to use vcpkg with Visual Studio, run the following command (may require administrator elevation):
PS C:\dev\vcpkg> .\vcpkg.exe integrate install
Applied user-wide integration for this vcpkg root.
CMake projects should use: "-DCMAKE_TOOLCHAIN_FILE=C:/dev/vcpkg/scripts/buildsystems/vcpkg.cmake"
All MSBuild C++ projects can now #include any installed libraries. Linking will be handled automatically. Installing new libraries will make them instantly available.
If everything went ok, libssh can be used in a C project in Visual Studio:
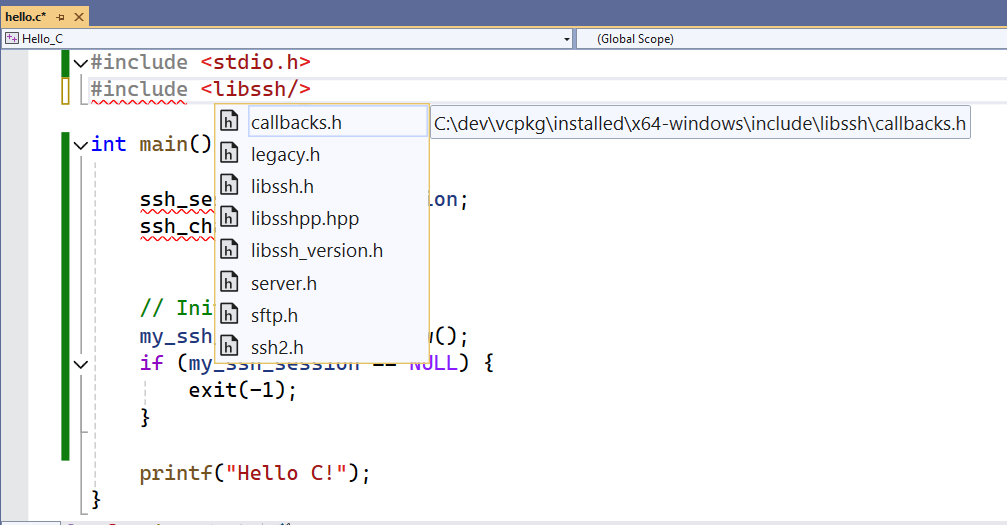
With this configuration, you can test out quick builds of the ssh_client.c application described in chapter APT Insights Part 2: Command and Control.
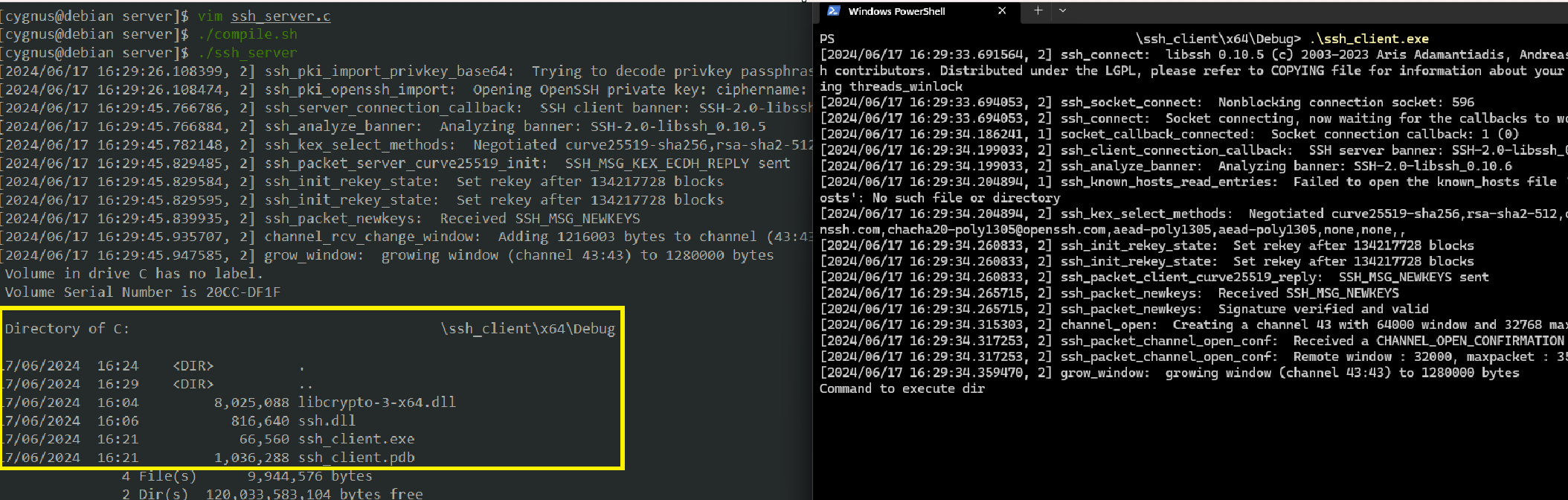
ssh_server/ssh_client.exe
As it can be seen below, we've got our first command execution ("dir") on a Windows target using the SSH client written in C.
(!) In the next chapter I'm going to glue the VBA/VBS dropper and this payload together to see if it's triggering the AV and what can we do to bypass it.
Stay tuned for more techniques, and remember: with great power comes great responsibility. Use this knowledge ethically and always with permission from the system owner.